The Industrial IoT Risks You Must Not Ignore in 2018
Scott Allen for Sys-Con Media: Security, therefore, will ultimately be the limiting factor on how much IoT technology is deployed.
SCADAfence Secures $10 Million in Funding to Protect Smart Manufacturing and Critical Infrastructure Networks from Cyber Attacks
Investors include JVP, NexStar Partners and Japan's Global Brain; funds will be used to boost go-to-market efforts and expand research and development operations
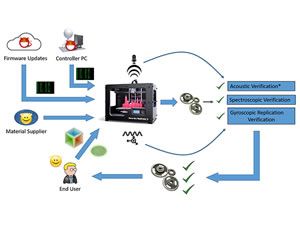
Defending 3D Printers From Hackers
Charles Q. Choi for IEEE Spectrum: Researchers reveal three methods of verifying that 3d-printed parts have not been compromised by someone hacking the printer itself.
The ioTrust Security Solution
Manufacturers who can uniquely identify individual parts in a secure manner have an advantage over the competition, which is struggling to master this new concept. With ioTrust, manufacturers can associate their products with a secure, unique identity, that can extend through the supply chain.
IIoT And The CyberThreat: A Perfect Storm Of Risk
Chris Grove for MBT Mag: Some organizations have a false sense of security and believe their industrial control systems cant be easily compromised.
Why PKI matters for the IIoT
Strong authentication of all devices within an IIoT network is one of the fundamental requirements for securing these networks.
Cybersecurity in the Factory
Technology for Industrial Control Systems and SCADA are now available that allow for continuous monitoring of these critical systems. A baseline is created and any deviations can be alerted and acted upon.
Manufacturers raise investment in next-gen tech, survey says
Dustin Walsh for Crain's Detroit Business: U.S. manufacturers are rapidly boosting investment in advanced digital technologies, according to a survey to be released Monday by Troy-based technology business association Automation Alley. The survey coincides with the association's 2017 Technology Industry Outlook event on Feb. 13 at the Detroit Institute of Arts. Nearly 400 manufacturing and technology business leaders are expected to attend.
According to the survey, 85 percent of U.S. manufacturing executives responded they plan to increase existing budgets for new technologies, with nearly a third planning to increase budgets by up to 15 percent. More than half of the respondents said they have a dedicated budget to technologies described as Industry 4.0, with the top three being cloud, cybersecurity and data analytics. Cont'd...
China Adopts Cybersecurity Law Despite Foreign Opposition
Bloomberg News: China has green-lit a sweeping and controversial law that may grant Beijing unprecedented access to foreign companies’ technology and hamstring their operations in the world’s second-largest economy.
The Cyber Security Law was passed by the Standing Committee of the National People’s Congress, China’s top legislature, and will take effect in June, government officials said Monday. Among other things, it requires internet operators to cooperate with investigations involving crime and national security, and imposes mandatory testing and certification of computer equipment. Companies must also give government investigators full access to their data if wrong-doing is suspected.
China’s grown increasingly aggressive about safeguarding its IT systems in the wake of Edward Snowden’s revelations about U.S. spying, and is intent on policing cyberspace as public discourse shifts to online forums such as Tencent Holdings Ltd.’s WeChat. The fear among foreign companies is that requirements to store data locally and employ only technology deemed “secure” means local firms gain yet another edge over foreign rivals from Microsoft Corp. to Cisco System Inc. Cont'd...
Smart Factory Hackathon: Talented data-science specialists develop solutions for the factory of the future
Press Release via AutomotiveWorld: “Data drives our production – you innovate from our data” is the motto of the Smart Factory Hackathon, which was held at the Audi Forum Ingolstadt from October 19 to 21. Talented young data-science specialists from the fields of IT, mathematics and engineering developed innovative software solutions for the factory of the future, based on genuine but anonymized data sets from Audi’s production. On Friday afternoon, the winners of the IT competition were awarded their prizes: The “Happy Unicorns” team won first prize with its idea on the subject of container management.
The Smart Factory Hackathon is a programmers’ marathon in which participants work out digital solutions and prototypes for genuine application cases over a period of 24 hours. For the competition, more than 20 departments from the pre-series center, toolmaking, paint shop, assembly and logistics had provided anonymized data sets with which the teams had to work. The results were assessed by a jury of four Audi experts and the startup consultant Thorsten Weber from “UnternehmerTUM,” the center for innovation and startups at the Technical University of Munich. The teams then presented their ideas to an audience. The winners were decided equally by the jury assessment and the audience’s votes. Cont'd...
3D printing hack: Researchers crash drone with sabotaged propeller
Conner Forrest for TechRepublic: University researchers were able to sabotage a drone by hacking the computer controlling the 3D printer that made its parts, according to a research paper released Thursday. By changing the design of the propellor before printing, they caused the $1,000 drone to "smash into the ground" and break, shortly after take off.
The paper, titled dr0wned - Cyber-Physical Attack with Additive Manufacturing, was a joint effort from researchers at Ben-Gurion University of the Negev (BGU), the University of South Alabama, and Singapore University of Technology and Design. In the paper, the researchers explained how they committed the cyberattack, and what the attack could mean for the future of 3D printing security.
Using a phishing attack, the researchers gained access to the PC that was connected to the 3D printer. Cont'd...
Owl Computing Technologies to Speak on Industrial Control System Cybersecurity in Japan
Owl to address top Japanese cybersecurity talent from critical infrastructure industries
Bosch, SAP team up for Industry 4.0
Peter Gutierrez for IoT Hub: Bosch and SAP will combine their expertise on cloud technologies and software solutions to make inroads into the Internet of Things and Industry 4.0 markets.
Customers will be able to use SAP’s HANA database platform within Bosch’s IoT Cloud, which the companies hope will enable large-scale data processing for IoT applications in real-time.
Bosch’s IoT microservices will also be made available in SAP’s HANA cloud platform, providing multiple device and component connectivity. Cont'd...
3D printed designs easily stolen by nearby smartphone
Jack Loughran for E&T: 3D printers have been shown to be vulnerable to attack by smartphones that can steal designs by being within close proximity during the printing process.
A study from the University at Buffalo, USA explored security vulnerabilities in 3D printing, also called additive manufacturing, which analysts say will become a multibillion-dollar industry employed to build everything from rocket engines to heart valves.
"Many companies are betting on 3D printing to revolutionise their businesses, but there are still security unknowns associated with these machines that leave intellectual property vulnerable," said assistant professor Wenyao Xu, who worked on the project. Cont'd...
Raytheon team competing in DARPA cyber competition finals
First-of-its-kind challenge tests fully automated, self-healing systems that defend against cyber attacks
Records 31 to 45 of 45
Featured Product

Super Air Knife Replaces Blowers & Saves Energy
Super Air Knife reduces compressed air usage & noise when compared to other blowoffs. The Super Air Knife offers a more efficient way to clean, dry or cool parts, webs or conveyors. It delivers a uniform sheet of laminar airflow across entire length.
https://exair.co/184_523
Manufacturing and Automation - Featured Company

The Wire Association International, Inc. (WAI)
The Wire Association International (WAI), Inc., founded in 1930, is a worldwide technical society for wire and cable industry professionals. Based in Madison, Connecticut, USA, WAI collects and shares technical, manufacturing, and general business information to the ferrous, nonferrous, electrical, fiber optic, and fastener segments of the wire and cable industry.
WAI hosts trade expositions, technical conferences, and educational programs.