Why B2B IAM Is Essential for Modern Manufacturing
Manufacturing plants create complex, segmented identity challenges that traditional Identity and Access Management (IAM) models weren’t designed to handle. IT teams must support a wide range of users, from corporate employees and engineers to plant floor workers and beyond. People use a wide variety of systems and devices and have very different access needs.
At the same time, external users such as auditors, contractors, distributors, and suppliers need secure access to ERP systems, quality control platforms, shared files, and even operational technology. Extensive collaboration with third parties is part of doing business, but it can also lead to security blind spots, operational risk, and compliance gaps.
Too often, external access is treated the same way as internal users are handled, or even worse. VPN access is widely used without strong safeguards regarding whether those users should be trusted or what they’re entitled to access. Cybercriminals are increasingly targeting VPN setups.
Unsurprisingly, ISO 27001:2022 has strengthened cybersecurity requirements, particularly around access control. This article explains why workforce IAM and IGA fall short in this environment, why B2B IAM is essential for modern manufacturing, enhances security, and how stronger access controls support evolving compliance standards.
Real-World Manufacturing Challenges
Manufacturers often grant broad VPN access to third parties without microsegmentation or device management. This level of access can expose ERP and operational systems to unmanaged endpoints, which traditional network segmentation doesn’t solve. Temporary users like contractors or visitors add complexity, while growing compliance demands (CMMC, ISO, NIST) require granular control, time-bound access, and tighter governance over external users.
Identity management tools aim to solve these challenges, but not all are built for the same purpose. No single solution fits every access need, especially in complex environments like manufacturing. Let’s explore the most common IAM solutions and where they fit.
Identity Management Solutions in Manufacturing
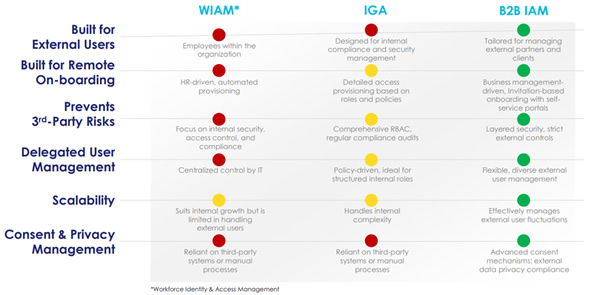
Workforce IAM Modernizes Legacy Directories
Workforce IAM is designed for employees using managed devices. It features HR-driven provisioning, role-based access control (RBAC), single sign-on (SSO), and conditional access policies. Increasingly, it also introduces phishing-persistent credentials. It works well in office environments but assumes users are permanent staff with long-term roles and company-issued equipment.
In manufacturing, those assumptions break down. External auditors access quality systems, contractors pull technical documentation, and distributors need to interact with ERP data. In many supplier-led industries, third parties also take part in product design, which requires access to R&D systems. These users work on devices managed by their own organizations, not yours, and their roles change frequently. Workforce IAM was not built to handle that kind of external collaboration.
IGA Aligns Access with Policies
Identity Governance and Administration (IGA) adds compliance and oversight to workforce IAM by managing entitlements, enforcing segregation of duties (SoD), and supporting access reviews and audit readiness. It can be helpful when ISO auditors come to pay a visit.
IGA is most effective for controlling internal access to sensitive systems like ERP, accounting, and R&D platforms. In manufacturing, IGA helps ensure strong role-based access among engineers, executives, and support staff.
However, it falls short when managing external users, temporary access, or device-agnostic environments that aren’t all centrally managed. It also normally doesn’t operate at runtime, meaning it can’t evaluate or enforce access decisions in the moment. Instead, it focuses on aligning access with policy over time.
VPN users also typically fall outside HR systems, limiting provisioning and identity lifecycle management.
B2B IAM is Made for External Collaboration
B2B IAM is purpose-built for external users and supports business-driven onboarding through delegated access and self-service portals. B2B IAM uses Relationship-Based Access Control (ReBAC) rather than traditional RBAC, allowing for more precise, context-aware permissions based on genuine business relationships.
It supports federated identities, allowing external users to log in with their own organization’s credentials when possible. But federation isn’t always available or practical. B2B IAM also enables secure onboarding for third parties without a modern identity provider, while still enforcing the same level of access control, policy compliance, and audit readiness.
These systems also support access from unmanaged devices and are better aligned with operational realities in manufacturing. B2B IAM helps organizations meet ISO 27001:2022 access control requirements and supports broader supply chain security and assurance initiatives.
As suppliers, contractors, and partners change, B2B IAM scales with them. It reduces onboarding delays, avoids manual access requests, and ensures that critical operations like production, logistics, inventories, or audits happen without disruption.
The following image provides an overview of the comparison between Workforce IAM, IGA, and B2B IAM.
Why B2B IAM Is a Strategic Investment
B2B IAM reduces IT overhead by enabling delegated user management and automating access workflows, making it easier to keep up with partner changes, like turnover or onboarding. It improves control and visibility across vendor and partner relationships, reducing the risk of unauthorized access. It also helps organizations stay compliant, resilient, and audit-ready while proactively aligning with ISO’s growing focus on access control, security, and accountability.
And when disruption hits, whether it is supplier turnover, an urgent onboarding need, or a shift in operational plans, B2B IAM ensures access does not become the blocker. It enables fast, policy-aligned access for external users without compromising security. That kind of flexibility helps organizations stay responsive and keep critical business processes moving, even when conditions change.
Conclusion
Workforce IAM and IGA are essential components of any identity strategy, but they aren’t enough on their own. External access in manufacturing environments is constant, complex, and high-risk without B2B IAM. It’s critical infrastructure for secure, scalable operations across today’s interconnected supply chains, where there’s no room for disruption or unfinished orders.
 Jose Caso, B2B IAM at Thales, is a seasoned product professional with over 15 years of experience in software development, product management, and product marketing. He specializes in aligning technical and business goals to deliver solutions that meet evolving client needs. With a background spanning physical security, cybersecurity, and enterprise solutions, Jose focuses on driving innovation that keeps businesses competitive in a dynamic market.
Jose Caso, B2B IAM at Thales, is a seasoned product professional with over 15 years of experience in software development, product management, and product marketing. He specializes in aligning technical and business goals to deliver solutions that meet evolving client needs. With a background spanning physical security, cybersecurity, and enterprise solutions, Jose focuses on driving innovation that keeps businesses competitive in a dynamic market.
Featured Product

